[ad_1]
The TA558 cyber crime group is behind a malware campaign targeting hospitality, hotel and travel firms in Latin America.
Prof Point researchers are tracking a malware campaign by a cybercrime group known as TA558 targeting hospitality, hotel and travel companies in Latin America.
The group employed several malware in its attacks, including Loda RAT, Vjw0rm and Revenge RAT, a small criminal threat actor that has been active since at least April 2018.
Repurposed malware to steal hotel customers’ personal and financial information, including credit card information, to perform lateral operations and deliver payloads.
The group is mainly targeting Portuguese and Spanish speakers, but experts have noticed attacks targeting entities in Western Europe and North America.
The gang’s activity increased in 2022, when the chain of attacks began phishing campaigns focused on reservations with lures such as hotel reservations.
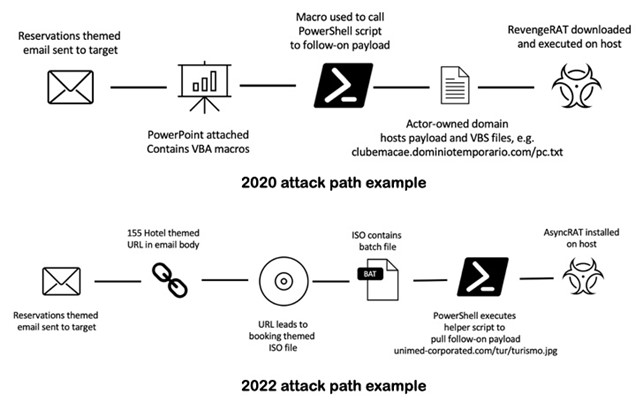
In 2022, ProfPoint has seen an increase in activity compared to previous years. In addition, TA558 changed tactics and started using URLs and container files to spread malware, probably because Microsoft announced that it will start blocking VBA macros downloaded from the Internet by default. Reads the analysis published by Proofpoint.
The attacks were carried out between 2018 and 2021, with emails containing tooled Word documents containing exploits or malicious macros. When you open the files, the infection process is started.

In recent attacks, the cyber crime group has started using malicious URLs, RAR attachments, ISO attachments and office documents to deliver malware. The move is a response to Microsoft’s decision to disable macros by default in Office products.
Proofpoint found that out of 51 campaigns by threat actors in 2022, 27 pointed URLs to ISO files and ZIP archives, while only five campaigns from 2018 to 2021 used this method.

Proofpoint reports that as of 2018, TA558 has used at least 15 different malware families, some of which use the same C2 infrastructure. Gangs deface hotel websites to host malicious payloads.
The threat actor changes languages several times in a week to avoid detection and profile of the attacks.
TA558 is using a number of popular patterns in campaign data, including the use of specific strings, conventions and keywords, domains, etc. For example, the attackers often used the term CDT in emails and malware attributes that were related to CDT traffic. Organization and related aspects of travel booking.
“TA558 is an active threat actor targeting the hospitality, travel and related industries since 2018. Activities by this actor can result in corporate and customer data as well as financial losses.” Summarize the report.
“Companies operating in targeted sectors, particularly in Latin America, North America and Western Europe, need to be aware of this actor’s strategies, techniques and processes.”
Follow me on Twitter: @ Security issues And Facebook
Pierluigi Paganini
(Safety issues – Hacking, TA558).
Share
[ad_2]
Source link