[ad_1]
Apple prides itself. It builds on the security measures built into the software and hardware – and will continue to add new safeguards and defenses over time. Lockdown Mode is a new feature headed to iPhones, iPads and Macs later this year, and it promises to protect your device from “highly targeted cyberattacks.”
As you can guess from the name, lockdown mode is like closing the shutters, double locking the doors and turning off all the lights in your house. It greatly limits the types of activities that are allowed on your devices, so that the damage is limited if something untoward happens.
For example, attachments other than images disappear in messages, and link previews are disabled. FaceTime calls from unknown numbers are blocked, as well as wired connections to other hardware and accessories. Shared albums are removed from the Photos app, and invitations to new shared albums are blocked.
On a more technical level, several web technologies are missing, including just-in-time (JIT) JavaScript compilation. example) cannot be loaded.
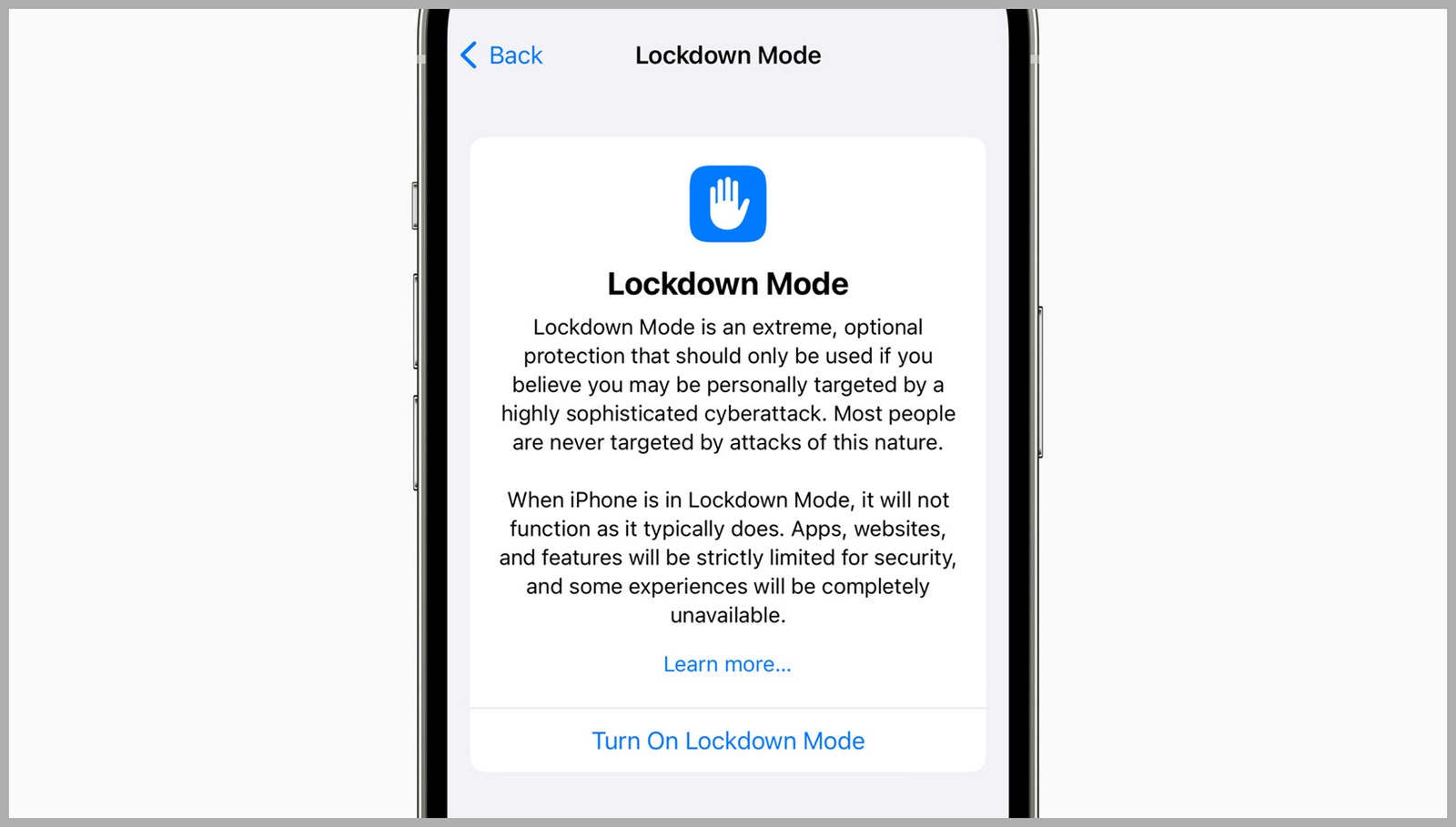
Lockdown mode is disabled by default but can be enabled on iPhone by going to settingsand then Privacy and securityand then Lock mode. Turning it on or off requires a system reset and a device PIN. Apple describes the feature as something for users at risk of “government-sponsored mercenary spyware”—which appears to be high-profile targets—anyone can turn it on for extra protection.
“Lockdown Mode is an extreme alternative defense that should only be used in the event of a highly sophisticated cyber attack that you believe could be personally targeted,” is how Apple puts it in its support document. “Most people are not the target of an attack of this nature.”
As Apple explains, the overall idea is to reduce the attack surface that malware and spyware can access. Tools including the Pegasus spyware package developed by the NSO team are capable of reading texts, monitoring calls, collecting passwords, tracking a user’s location, and more—and some require no interaction from the user.
With Pegasus, for example, a WhatsApp call to the target device is all it takes for the spyware to start its work, even if the call is not answered. This particular piece of spyware has been blocked from running on devices running iOS 15 or higher, but it’s worth noting that many other threats still exist, and there are more to come.
[ad_2]
Source link