[ad_1]
It’s no big secret that tech companies like Meta, TikTok, and Google track their users’ activities as closely as possible, but a new web tool is exposing just how covertly (and sadly) they do it. Last week, security researcher and former Google employee Felix Krauss wrote an article explaining how businesses can inject JavaScript code into third-party websites visited by apps like Instagram and Facebook to track everything they do and click. Following his readers’ understandably anxious responses, Krause went on to build a website called InAppBrowser.com, which shows you a large portion of what companies can see — large, but unfortunately not comprehensive.
[ Related: “You have the power to protect your data. Own it.“ ]
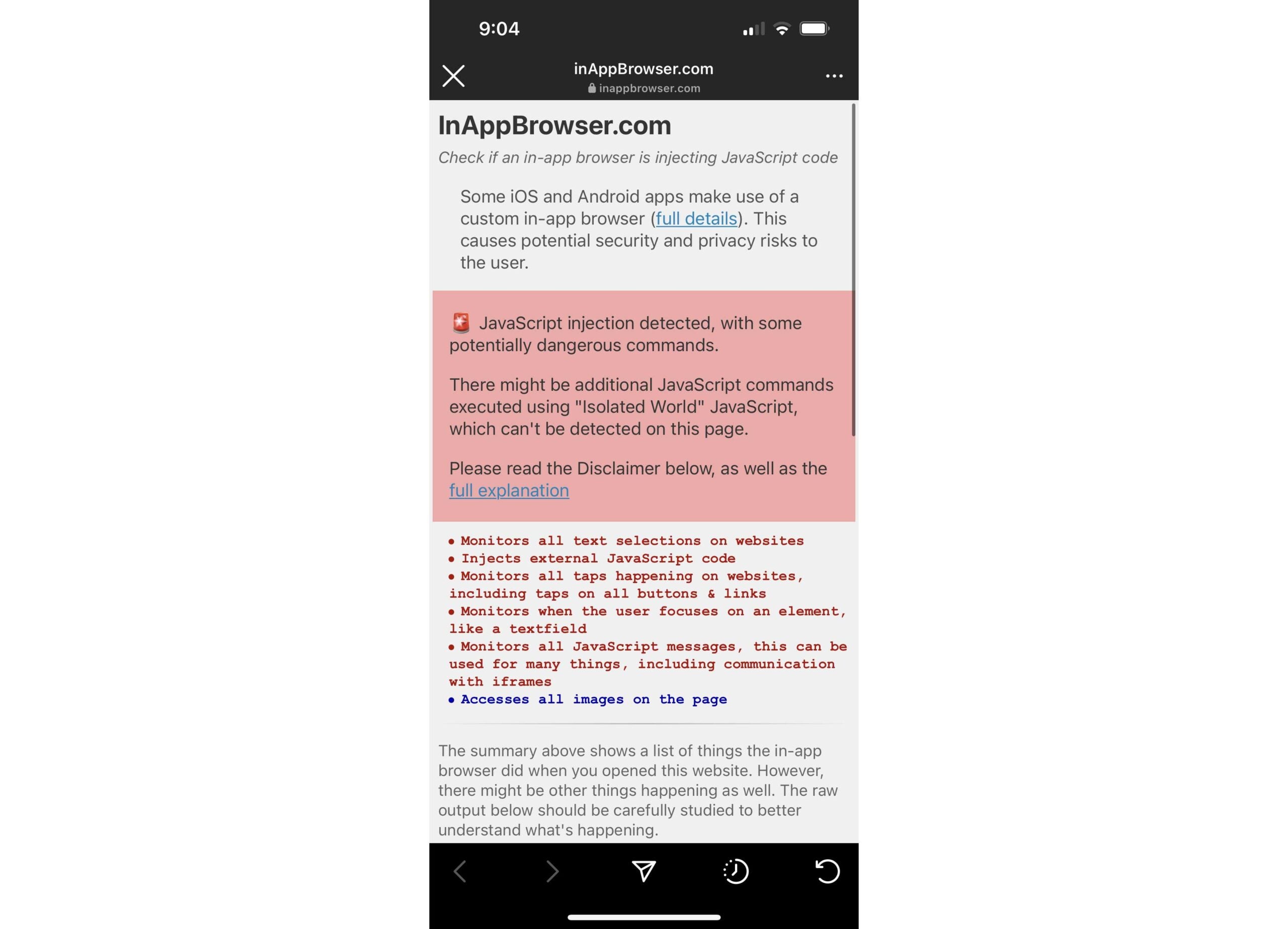
Krause’s InAppBrowser can show you at least some of these tracking methods by opening the website inside the app. As he notes in the post, however, “there is no way for us to know the full details of what data each in-app browser collects, or how or if that data is transmitted or used.” [InAppBrowser] It is describing the JavaScript commands that are executed by each application, and what effect each command can have.
To use InAppBrowser, all you need to do is copy the full website address.https://inappbrowser.com/) and paste it as a clickable link in the app of your choice. On Instagram, for example, you can make a dummy post (like an Instagram story created just to host the link), send a direct message with the link, or post the link in your profile bio. Then just click on the link in the app to open the in-app browser and view the results.
Popsky Tested the site in Instagram and received the following report
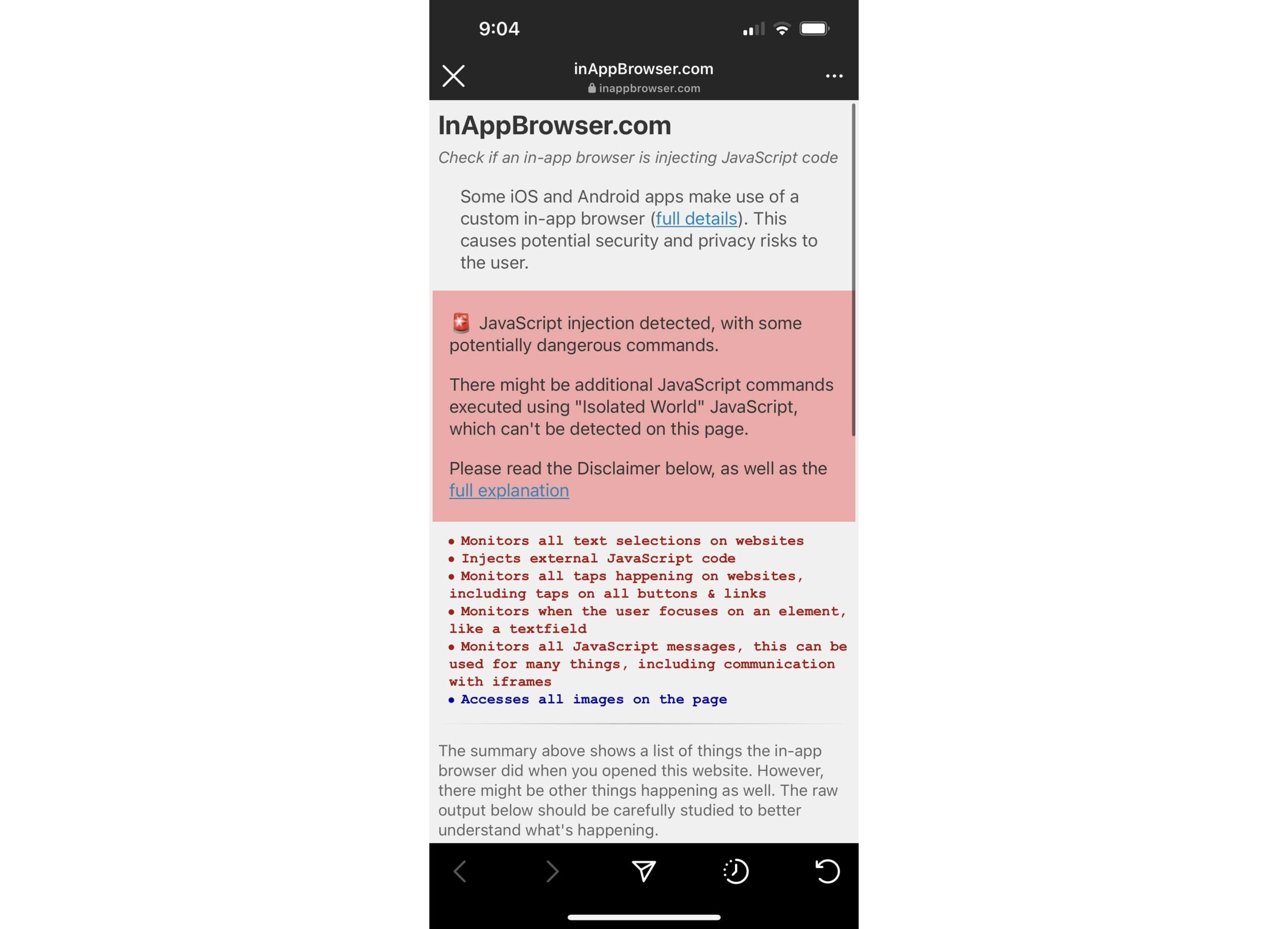
such as Verge He explains, “In-app browsers are used when you click on a URL within an app. While these browsers are based on Safari’s WebKit on iOS, developers can modify them to run their own JavaScript code, allowing them to track your activity without your consent or the third-party websites you visit. Which is exactly what happens. Everything from keystrokes, highlighted text to clicked links can be tracked, along with additional personal information such as usernames, passwords and phone numbers. Although it’s unclear what companies like Meta will do with that information, Krause suggests that bad actors could use their own JavaScript exploits to exploit security holes.
[ Related: “Apple pushes for more in-app ads” ]
Although the InAppBrowser tool is not complete, Krause has made sure to make the entire source code available open source on GitHub, a site for future community access, analysis, and improvement. And while it’s unlikely that any of the companies will remove JavaScript code anytime soon, it’s best to simply copy and paste any link you need in the future and open it in your browser of choice.
[ad_2]
Source link